Decoding User Datagram Protocol (UDP)
Internet Protocols are used to send IP datagrams across a network to their destination based on the IP address of the destination endpoint. But this protocol does not provide any information about which application is suppose to consume the datagram.
Each endpoint or host has many applications running with different process id. But these process ids keep changing whenever the application or server is rebooted and a new process id is launched. So we need to mechanism through which it would easier to identify the application on a particular host rather than depending on its process id.
User Datagram Protocol
In TCP/IP protocol suite, the UDP protocol provides the primary mechanism that application programs use to send datagrams to other application programs. UDP messages uniquely identify each application running on a host or endpoint using the protocol port number which is unique for each application.
UDP provides applications with the same best-effort, connectionless datagram delivery semantics as IP. UDP does not guarantee that messages arrive, does not guarantee messages arrive in the same order they are sent, and does not provide any mechanisms to control the rate at which information flows between a pair of communicating hosts.
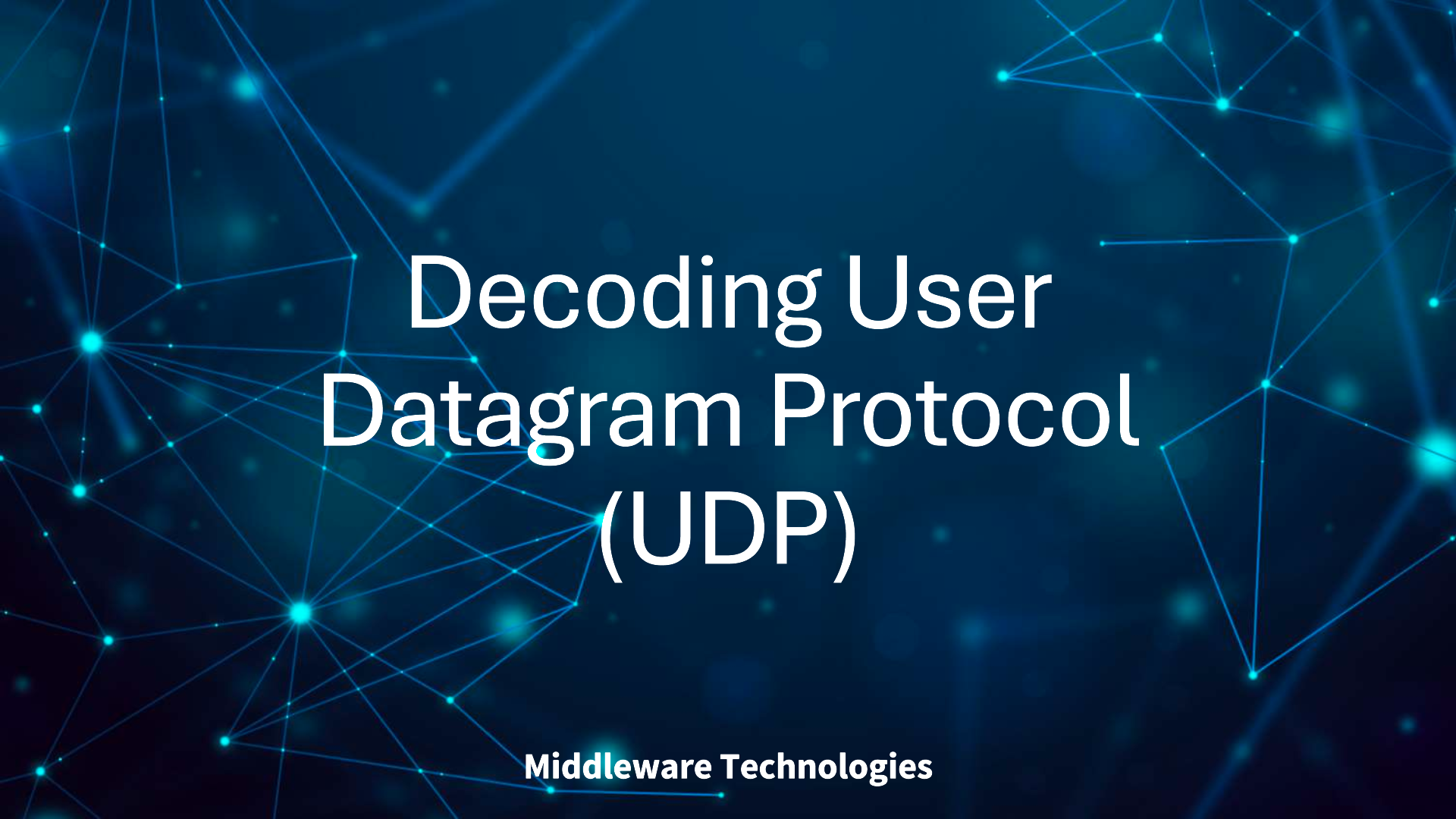
UDP Message Format
UDP message contains both destination port and source port numbers which helps the message to be delievered to the correct destination and the receiver to send back a reply to the correct source application port.
- UDP Source Port: It contains a 16-bit protocol port number used by the sending application.
- UDP Destination Port: It contains a 16-bit protocol port number used by the receiving application.
- UDP MESSAGE LENGTH: It contains the count of octets in the UDP datagram, including the UDP header and the user data
- UDP CHECKSUM: IPv4 and IPv6 differ in their interpretation of the UDP CHECKSUM field. For IPv6, the UDP checksum is required. For IPv4, the UDP checksum is optional and need not be used at all; a value of zero in the CHECKSUM field means that no checksum has been computed (i.e., a receiver should not verify the checksum).
UDP checksum is calculated using the UDP header, UDP payload and additional information extracted from the IP header. This additional information which is extracted from IP is known as pseudo-header.
The pseudo-header used in the UDP checksum computation for IPv4 consists of 12 octets of data whereas in IPv6 it consists of 40 octets of data.
UDP Protocol in TCP/IP Layer
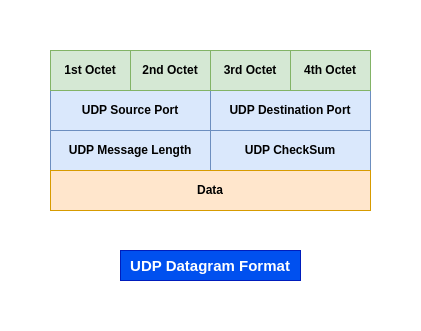
UDP Protcol springs into action at the Transport Layer of the TCP/IP protocol suite above the IP protocol. A complete UDP message, including the UDP header and payload, is encapsulated in an IP datagram as it travels across an internet.
The above IP datagram is encapsulated in a network frame as it travels across an underlying network, which means there are two levels of encapsulation.
The IP layer is responsible only for transferring data between a pair of hosts on an internet, while the UDP layer is responsible only for differentiating among multiple sources or destinations within one host.
UDP Protocol software maintains a queue holding the UDP datagram that are received. The algorithim tries to match if the destination ports matches with any port on the receiving host and forwards the datagram to that respective application.
If the destination port does not match or the port is full and unable to accept any more UDP message, the receiver will send a ICMP message indicating with an error.
UDP Port Assignment
The applications running on two hosts or endpoints that want to communicate a message need to know the port numober being used by the application. There are two fundamental approaches that are used when the port assignment occurs to applications.
- Universal assignment: In this case ports are assigned by a central authority for popular applications. Software is built according to the list. These ports are also know as well-known port assignments.
- Dynamic assignment: In the dynamic binding approach, ports are not globally known. Instead, whenever an application program needs a protocol port number, protocol software in the operating system chooses an unused number and assigns it to the application. When an application needs to learn the current protocol port assignments on another computer, the application must send a request that asks for a port assignment.
The well-known port numbers assigned by the central authority begin at low values and extend upward, leaving larger integer values available for dynamic assignment.
Here is the list of well known port assignments.
Hope you enjoyed reading this article. Thank you..
Leave a Reply
You must be logged in to post a comment.