How to setup sonarqube for code review and email notification

Here in this article we will how we can setup a sonarqube server and scan a python based project using sonarqube scanner. Once the code review is completed we will see how we can setup a email notification in the sonarqube server for any failures in the code quality review and other events for which we want to be notified.
Test Environment
Fedora 35 server
What is Sonarqube
Sonarqube is a code review and analysis tool. It helps in reviewing the code quality and analyse it to identify any bugs or vulnerabilities. It’s help the developers know about their code and get it sorted out during the software build cycle. There are two parts of this tool one is the sonarqube server which provides an interface to developers with the code review reports and feedback and other is sonarqube scanner which is a tool used to scan the code and analyse it which is further posted to the sonarqube server.
Procedure
Step1: Instantiate sonarqube container
As a first step we need to have a sonarqube server so we are going to setup it as a docker server using the 8.9 version community edition of the sonarqube image as shown below. Once the docker service is up and running you can launch the sonarqube web interface on the default port 9000 exposed on port 9000 on host machine.
[admin@fedser32 sonarqube_notify]$ docker run -d --name sonarqube -e SONAR_ES_BOOTSTRAP_CHECKS_DISABLE=true -p 9000:9000 sonarqube:8.9-community
[admin@fedser32 sonarqube_notify]$ docker logs -f sonarqube
...
2022.02.08 06:44:58 INFO ce[][o.s.p.ProcessEntryPoint] Starting ce
2022.02.08 06:44:58 INFO ce[][o.s.ce.app.CeServer] Compute Engine starting up...
2022.02.08 06:44:58 INFO ce[][o.s.s.e.EsClientProvider] Connected to local Elasticsearch: [http://localhost:9001]
2022.02.08 06:44:59 INFO ce[][o.sonar.db.Database] Create JDBC data source for jdbc:h2:tcp://127.0.0.1:9092/sonar
2022.02.08 06:44:59 WARN ce[][o.s.db.dialect.H2] H2 database should be used for evaluation purpose only.
2022.02.08 06:45:00 INFO ce[][o.s.s.p.ServerFileSystemImpl] SonarQube home: /opt/sonarqube
2022.02.08 06:45:00 INFO ce[][o.s.c.c.CePluginRepository] Load plugins
2022.02.08 06:45:01 INFO ce[][o.s.c.c.ComputeEngineContainerImpl] Running Community edition
2022.02.08 06:45:01 INFO ce[][o.s.ce.app.CeServer] Compute Engine is operational
2022.02.08 06:45:01 INFO app[][o.s.a.SchedulerImpl] Process[ce] is up
2022.02.08 06:45:01 INFO app[][o.s.a.SchedulerImpl] SonarQube is up
...
URL - http://fedser32.stack.com:9000/
Step2: Create a project manually
Here in this step we will create a new project in sonarqube server using the manual procedure and provide the required details. In my case i have created a project with the following details.
Project key - alerta
Display name - alerta
Token - alerta: 128ebf6371f5768609217f4334bbc1829cb68a91
Based on the project type and operation system that you choose it will provide you with the options to download the sonarqube scanner and execute it to scan that particular project. In my case i am choosing to scan a python based project on linux OS.
Step3: Download and configure a Python based project
As i am choosing to scan a python based project on linux OS. I am downloading a sample alert monitoring project named ‘alerta’ as shown below. Also i have created a sonar-project.properties file in the base directory of the python project by setting the projectKey as shown below.
[admin@fedser32 sonarqube_notify]$ git clone https://github.com/alerta/alerta.git
[admin@fedser32 sonarqube_notify]$ cd alerta/
Create a sonar project configuration file in the base directory of the sample project.
[admin@fedser32 alerta]$ cat sonar-project.properties
# must be unique in a given SonarQube instance
sonar.projectKey=alerta
# --- optional properties ---
# defaults to project key
#sonar.projectName=My project
# defaults to 'not provided'
#sonar.projectVersion=1.0
# Path is relative to the sonar-project.properties file. Defaults to .
#sonar.sources=.
# Encoding of the source code. Default is default system encoding
#sonar.sourceEncoding=UTF-8
Step4: Instantiate SonarScanner container
Based on the type of project and os platform you will be provided with the options to Download and Executhe scanner as shown below.
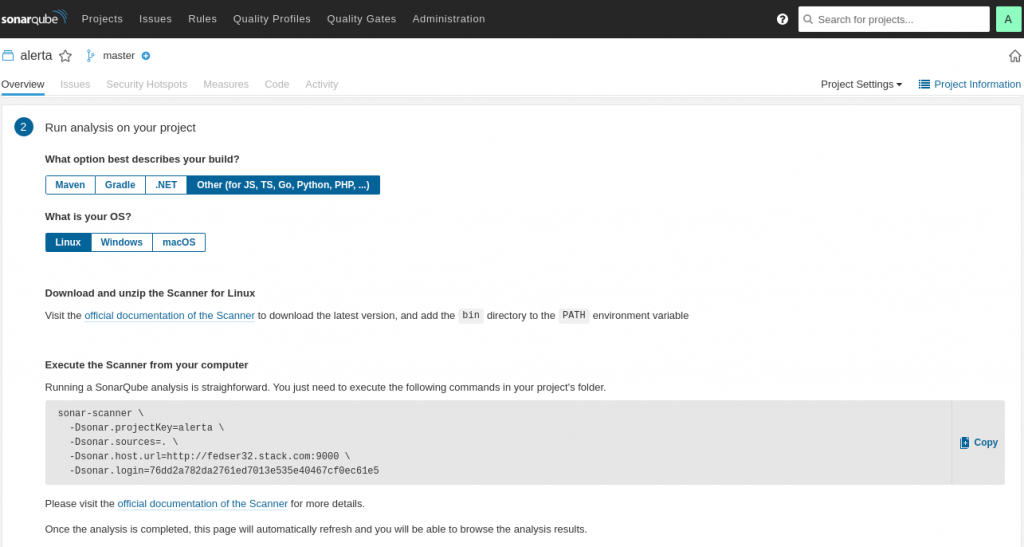
Let’s instantiate sonar scanner container with required inputs. For the sonarqube scanner to post the scan results to the sonarqube server it needs to authenticate with the sonarqube server which is done using the token key which is passed as SONAR_LOGIN parameter while running the sonar scanner.
[admin@fedser32 alerta]$ docker run --rm -e SONAR_HOST_URL="http://192.168.29.117:9000" -e SONAR_LOGIN="128ebf6371f5768609217f4334bbc1829cb68a91" -v "/home/admin/middleware/stack/docker/projects/sonarqube_notify/alerta:/usr/src" sonarsource/sonar-scanner-cli
INFO: Scanner configuration file: /opt/sonar-scanner/conf/sonar-scanner.properties
INFO: Project root configuration file: /usr/src/sonar-project.properties
INFO: SonarScanner 4.6.2.2472
INFO: Java 11.0.14 Alpine (64-bit)
INFO: Linux 5.16.5-200.fc35.x86_64 amd64
INFO: User cache: /opt/sonar-scanner/.sonar/cache
INFO: Scanner configuration file: /opt/sonar-scanner/conf/sonar-scanner.properties
INFO: Project root configuration file: /usr/src/sonar-project.properties
INFO: Analyzing on SonarQube server 8.9.7
INFO: Default locale: "en_US", source code encoding: "UTF-8" (analysis is platform dependent)
INFO: Load global settings
INFO: Load global settings (done) | time=54ms
INFO: Server id: BF41A1F2-AX7YE7iVHym6nUpCutrb
INFO: User cache: /opt/sonar-scanner/.sonar/cache
INFO: Load/download plugins
INFO: Load plugins index
INFO: Load plugins index (done) | time=35ms
INFO: Load/download plugins (done) | time=946ms
INFO: Process project properties
INFO: Process project properties (done) | time=0ms
INFO: Execute project builders
INFO: Execute project builders (done) | time=1ms
INFO: Project key: alerta
INFO: Base dir: /usr/src
INFO: Working dir: /usr/src/.scannerwork
INFO: Load project settings for component key: 'alerta'
INFO: Load project settings for component key: 'alerta' (done) | time=21ms
INFO: Load quality profiles
INFO: Load quality profiles (done) | time=58ms
INFO: Load active rules
INFO: Load active rules (done) | time=1743ms
INFO: Indexing files...
INFO: Project configuration:
INFO: Load project repositories
INFO: Load project repositories (done) | time=35ms
INFO: 210 files indexed
INFO: 0 files ignored because of scm ignore settings
INFO: Quality profile for js: Sonar way
INFO: Quality profile for py: Sonar way
INFO: Quality profile for web: Sonar way
INFO: ------------- Run sensors on module alerta
INFO: Load metrics repository
INFO: Load metrics repository (done) | time=33ms
INFO: Sensor Python Sensor [python]
INFO: Starting global symbols computation
INFO: 148 source files to be analyzed
INFO: 142/148 files analyzed, current file: tests/test_isa_18_2.py
INFO: 148/148 source files have been analyzed
INFO: Starting rules execution
INFO: 148 source files to be analyzed
INFO: 148/148 source files have been analyzed
INFO: Sensor Python Sensor [python] (done) | time=15263ms
INFO: Sensor Cobertura Sensor for Python coverage [python]
INFO: Sensor Cobertura Sensor for Python coverage [python] (done) | time=51ms
INFO: Sensor PythonXUnitSensor [python]
INFO: Sensor PythonXUnitSensor [python] (done) | time=4ms
INFO: Sensor CSS Rules [cssfamily]
INFO: 7 source files to be analyzed
INFO: 7/7 source files have been analyzed
INFO: Sensor CSS Rules [cssfamily] (done) | time=1038ms
INFO: Sensor JaCoCo XML Report Importer [jacoco]
INFO: 'sonar.coverage.jacoco.xmlReportPaths' is not defined. Using default locations: target/site/jacoco/jacoco.xml,target/site/jacoco-it/jacoco.xml,build/reports/jacoco/test/jacocoTestReport.xml
INFO: No report imported, no coverage information will be imported by JaCoCo XML Report Importer
INFO: Sensor JaCoCo XML Report Importer [jacoco] (done) | time=2ms
INFO: Sensor JavaScript analysis [javascript]
INFO: 3 source files to be analyzed
ERROR: Browserslist: caniuse-lite is outdated. Please run:
ERROR: npx browserslist@latest --update-db
ERROR:
ERROR: Why you should do it regularly:
ERROR: https://github.com/browserslist/browserslist#browsers-data-updating
INFO: 3/3 source files have been analyzed
INFO: Sensor JavaScript analysis [javascript] (done) | time=3175ms
INFO: Sensor TypeScript analysis [javascript]
INFO: No input files found for analysis
INFO: Sensor TypeScript analysis [javascript] (done) | time=1ms
INFO: Sensor C# Project Type Information [csharp]
INFO: Sensor C# Project Type Information [csharp] (done) | time=0ms
INFO: Sensor C# Properties [csharp]
INFO: Sensor C# Properties [csharp] (done) | time=1ms
INFO: Sensor JavaXmlSensor [java]
INFO: Sensor JavaXmlSensor [java] (done) | time=1ms
INFO: Sensor HTML [web]
INFO: Sensor HTML [web] (done) | time=67ms
INFO: Sensor VB.NET Project Type Information [vbnet]
INFO: Sensor VB.NET Project Type Information [vbnet] (done) | time=1ms
INFO: Sensor VB.NET Properties [vbnet]
INFO: Sensor VB.NET Properties [vbnet] (done) | time=1ms
INFO: ------------- Run sensors on project
INFO: Sensor Zero Coverage Sensor
INFO: Sensor Zero Coverage Sensor (done) | time=66ms
INFO: SCM Publisher SCM provider for this project is: git
INFO: SCM Publisher 152 source files to be analyzed
INFO: SCM Publisher 152/152 source files have been analyzed (done) | time=2907ms
INFO: CPD Executor 16 files had no CPD blocks
INFO: CPD Executor Calculating CPD for 142 files
INFO: CPD Executor CPD calculation finished (done) | time=100ms
INFO: Analysis report generated in 82ms, dir size=2 MB
INFO: Analysis report compressed in 237ms, zip size=985 KB
INFO: Analysis report uploaded in 34ms
INFO: ANALYSIS SUCCESSFUL, you can browse http://192.168.29.117:9000/dashboard?id=alerta
INFO: Note that you will be able to access the updated dashboard once the server has processed the submitted analysis report
INFO: More about the report processing at http://192.168.29.117:9000/api/ce/task?id=AX7YSMBFHym6nUpCuyct
INFO: Analysis total time: 37.322 s
INFO: ------------------------------------------------------------------------
INFO: EXECUTION SUCCESS
INFO: ------------------------------------------------------------------------
INFO: Total time: 39.175s
INFO: Final Memory: 232M/787M
INFO: ------------------------------------------------------------------------
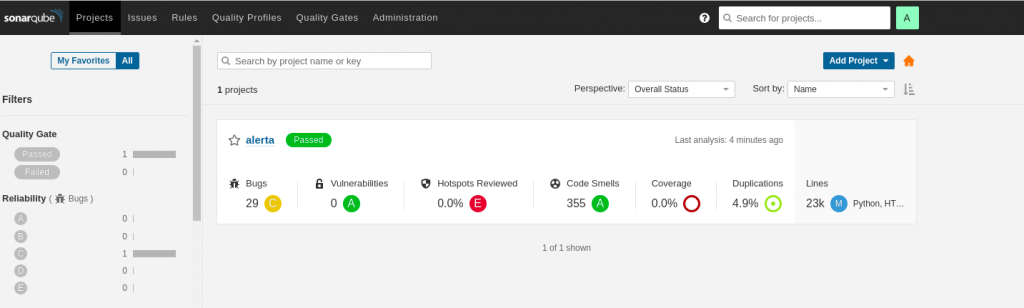
Step5: Validate the Sonar Scanner results
Now we have the sonarscanner results posted onto the sonarqube server web interface with all the details about the code review.
Step6: Sonarqube Email configuration
Now that we have the sonarqube server and sonarqube scanner setup ready with a python project. Let’s carry out the email configuration with the below bash script.
Let me provide brief details about each function that i have defined below.
resetpassword – This function helps in resetting the default admin:admin password of the sonarqube server with the adminuser and adminpassword that you want to setup. If you have already reset the admin password you can comment out this function.
configuresmtp – This function is going to configure the smtp server setting like the smtpserver, smtpserver port, from and prefix settings.
createuser – This function is going to create a new user who will subscribe to the email notifications for getting the code review events
subscribeusernotify – This function needs to be executed with the user that we just created. It subscribes the user to the required sonarqube code review events.
[admin@fedser32 sonarqube_notify]$ cat sonar_emailconfig.sh
#!/bin/bash
adminuser=admin
#defaultpassword=admin
adminpassword=admin@1234
devuser=devsonar
devpassword=devsonar
baseurl=http://localhost:9001
email=xxx@gmail.com
# Reset admin password
resetpassword()
{
echo "Reset admin password"
curl -u $adminuser:$defaultpassword -X POST "$baseurl/api/users/change_password?login=$adminuser&previousPassword=$defaultpassword&password=$adminpassword"
}
# Configure smtp server settings
configuresmtp()
{
echo "Configure smtp server settings"
curl -u $adminuser:$adminpassword -X POST "$baseurl/api/settings/set?key=email.prefix&value=%5BSONARQUBE%5D"
curl -u $adminuser:$adminpassword -X POST "$baseurl/api/settings/set?key=email.from&value=xxx@gmail.com"
curl -u $adminuser:$adminpassword -X POST "$baseurl/api/settings/set?key=email.fromName&value=xxx"
curl -u $adminuser:$adminpassword -X POST "$baseurl/api/settings/set?key=email.smtp_host.secured&value=<smtpserver>"
curl -u $adminuser:$adminpassword -X POST "$baseurl/api/settings/set?key=email.smtp_port.secured&value=<smtpport>"
}
# Create user
createuser()
{
echo "Create user"
curl -u $adminuser:$adminpassword -X POST "$baseurl/api/users/create?login=$devuser&name=$devuser&password=$devpassword&email=$email"
}
# Subscribe user to code review notifications
subscribeusernotify()
{
echo "Subscribe user to code analysis notifications"
curl -u $devuser:$devpassword -X POST "$baseurl/api/notifications/add?type=CeReportTaskFailure"
curl -u $devuser:$devpassword -X POST "$baseurl/api/notifications/add?type=ChangesOnMyIssue"
curl -u $devuser:$devpassword -X POST "$baseurl/api/notifications/add?type=NewAlerts"
curl -u $devuser:$devpassword -X POST "$baseurl/api/notifications/add?type=SQ-MyNewIssues"
}
### To be carried out by admin user
#resetpassword
configuresmtp
createuser
### To be carried out by normal user
subscribeusernotify
If you want to carry out the email configuration from web interface it can be done by Administration – General settings for email setting and for creating new user you can navigate to Security – Users settings.
With this our sonarqube server and scanner setup is completed. Once any project review quality gate status changes you should be able to get the notification to the email address for the user subscribed to the notification. Also the script assumes you have non ssl based smtp server setup in your environment without any authentication required for which only the smtp server and port details would be sufficient.
Hope you enjoyed reading this article. Thank you..
Leave a Reply
You must be logged in to post a comment.