How to manage users and roles for an OpenSearch cluster

Here in this article we will try to setup a OpenSearch Cluster on a local machine and try to configure its users and roles for secure access.
Test Environment
- Fedora 41 server
- Docker version 27.4.1
- Docker Compose v2.32.1
What is OpenSearch
OpenSearch is open source distribution of Elasticsearch with advanced features like Vector Search, AI/ML integrated search applications, Application and infrastructure monitoring, Anamoly detection and more enabled using the respective plugins.
The security plugin that is installed and enabled by default with OpenSearch comes with a default set of internal users which can be used to manage the OpenSearch cluster. These internal user are authenticated using the internal user database which is a yaml file with hash passwords and roles attached.
Here in this article we will see how we can create a new user, create a new role and map the new user with the new role to provide the required level of access to manage the OpenSearch cluster.
- Using the OpenSearch Dashboard
- Using the Security Plugin REST API
These are two ways we can manage users and roles at a broad level in the OpenSearch cluster.
If you are interested in watching the video. Here is the YouTube video on the same step by step procedure outlined below.
Procedure
Step1: Setup the OpenSearch cluster using docker compose file
Follow “How to setup Opensearch and Opensearch Dashboard” to setup a OpenSearch Cluster on a local machine.
OpenSearch service validation
admin@linuxser:~/opensearch$ curl https://linuxser.stack.com:9200 -ku admin:Se@rch@2025
{
"name" : "opensearch-node1",
"cluster_name" : "opensearch-cluster",
"cluster_uuid" : "xcaIsJtWSE-F_iBXmzv9Kg",
"version" : {
"distribution" : "opensearch",
"number" : "3.2.0",
"build_type" : "tar",
"build_hash" : "6adc0bf476e1624190564d7fbe4aba00ccf49ad8",
"build_date" : "2025-08-12T03:55:01.226522683Z",
"build_snapshot" : false,
"lucene_version" : "10.2.2",
"minimum_wire_compatibility_version" : "2.19.0",
"minimum_index_compatibility_version" : "2.0.0"
},
"tagline" : "The OpenSearch Project: https://opensearch.org/"
}
OpenSearch Dashboard service validation
URL: http://linuxser.stack.com:5601/
Step2: Create user using the OpenSearch Dashboard
First login to the OpenSearch dashboard and navigate to Security tab under Management as shown in below figure.
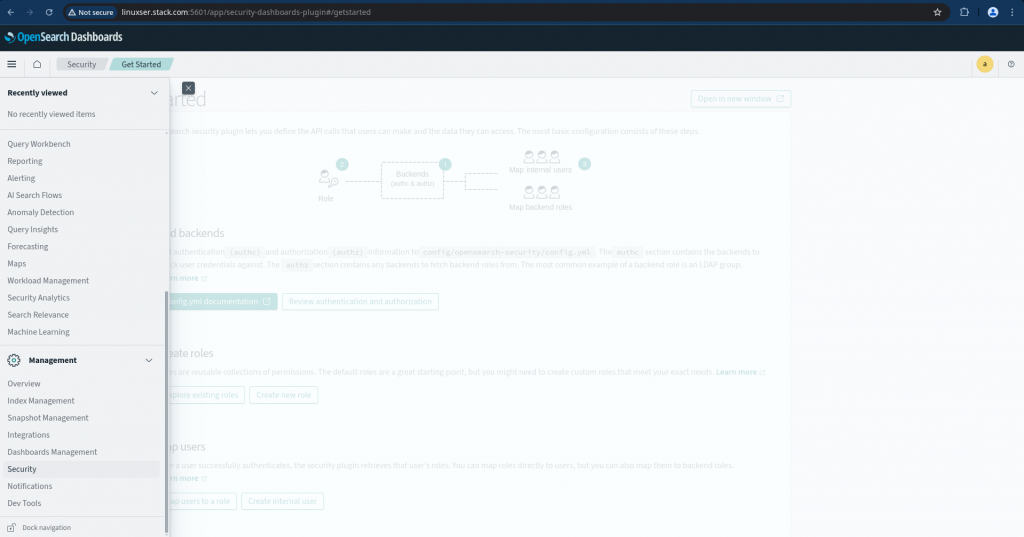
Once you are into the security tab you will get to see various options to manage users, roles, permissions and others as shown below.
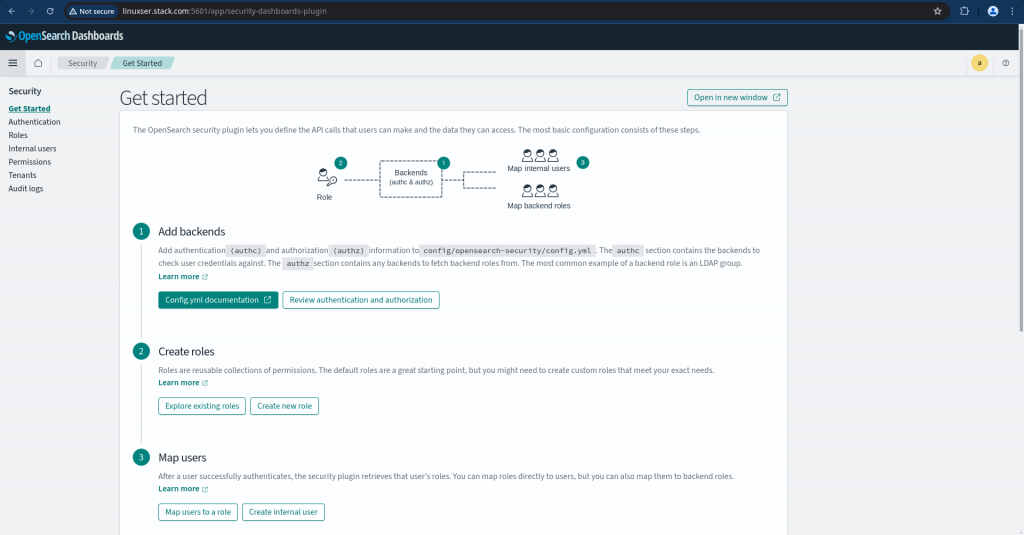
In this article as mentioned previously we will be using the internal user database. Navigate to “Internal users” and click on “Create internal user” to create a new user named “devuser1” with password “devuser@2025”. For production environment setup make sure you have a strong password setup as per your organisations password policy for security purpose.
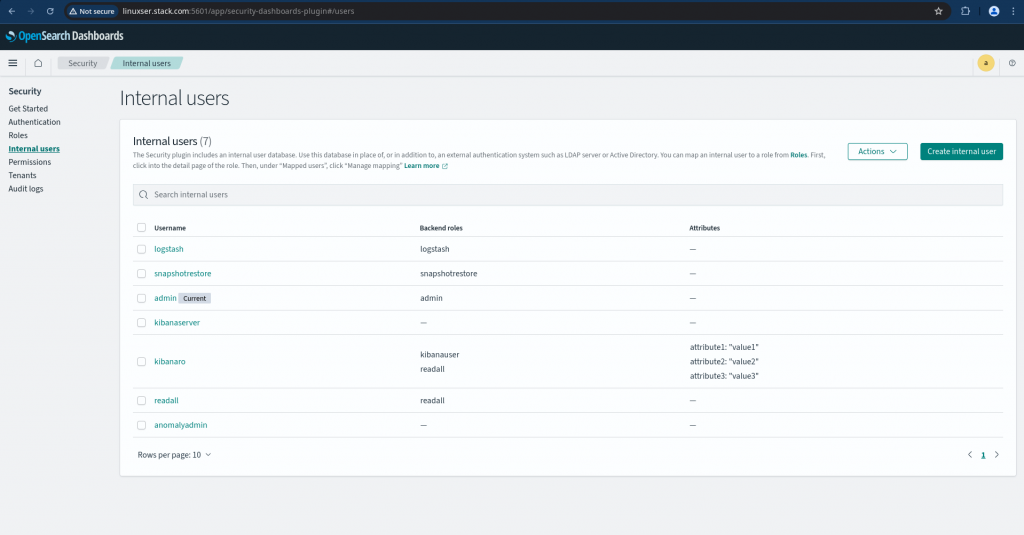
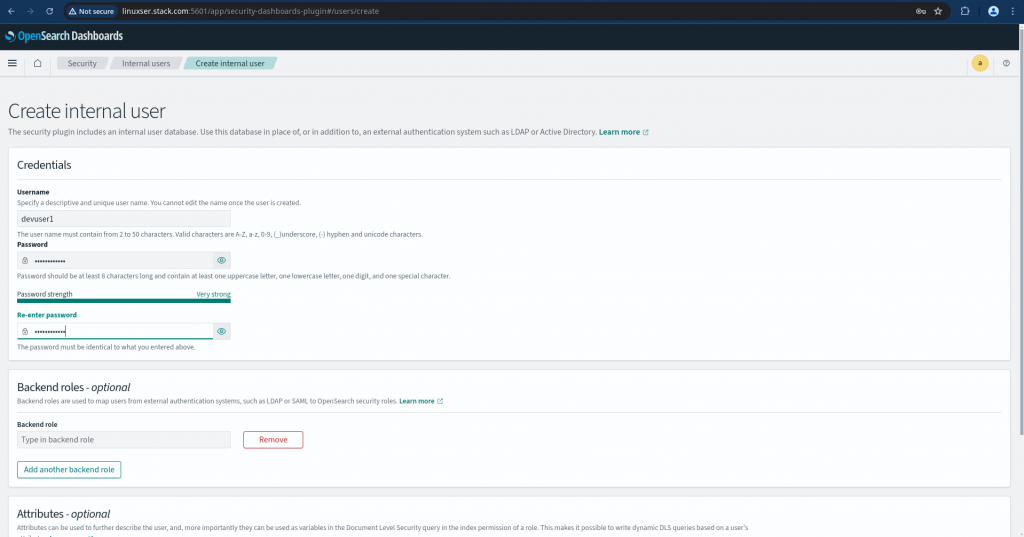
Once created you should be able to see the new user in the list of internal user as shown below.
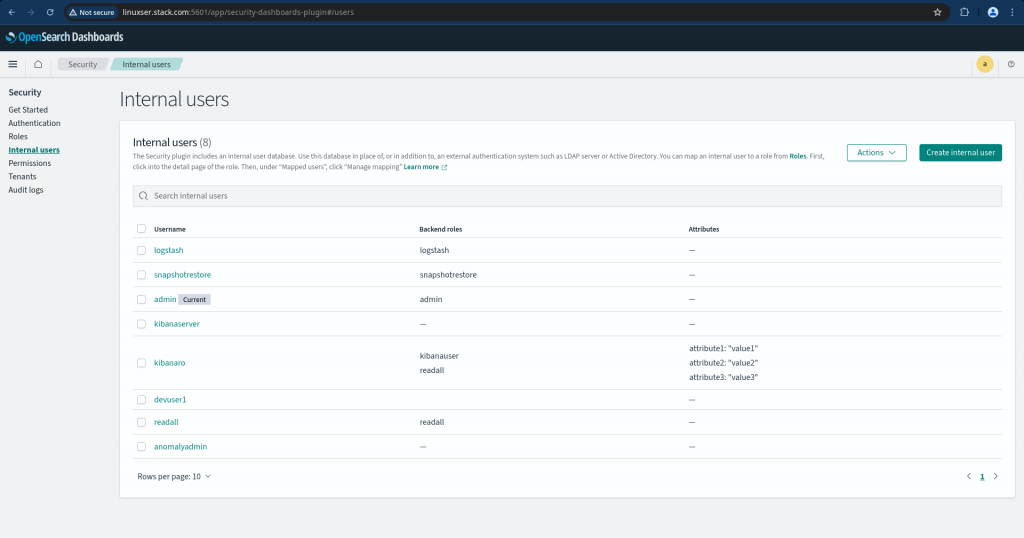
Step3: Create role using the OpenSearch Dashboard
Now we have an user named ‘devuser1’ created but that user does not have any permissions set to manage the cluster or indexes and do other operations as permitted or required.
For a user to have the required permissions we first need to create a role with the set of required permissions. Let’s navigate to Roles tab under Security and Click on Create role button to get to the page.
The create role page can be divided into four sections to update as shown below.
- Name – Provide a descriptive name for the role
- Cluster Permissions – Specify how users in this role can access the cluster. By default, no cluster permission is granted
- Index Permissions – Specify how users in this role can access the specific indices. By default, no index permission is granted
- Tenant Permissions – Tenants are useful for safely sharing your work with other OpenSearch users. You can control which roles have access to a tenant and whether those roles have read and/or write access
Here, lets create a new role named ‘devuser1Role’ with Cluster and Index level permissions as shown below.
Role Name: devuser1Role
Cluster Permissions:
Cluster Permissions: "cluster_all"
Index Permissions:
Index: "*"
Permissions: "indices_all"
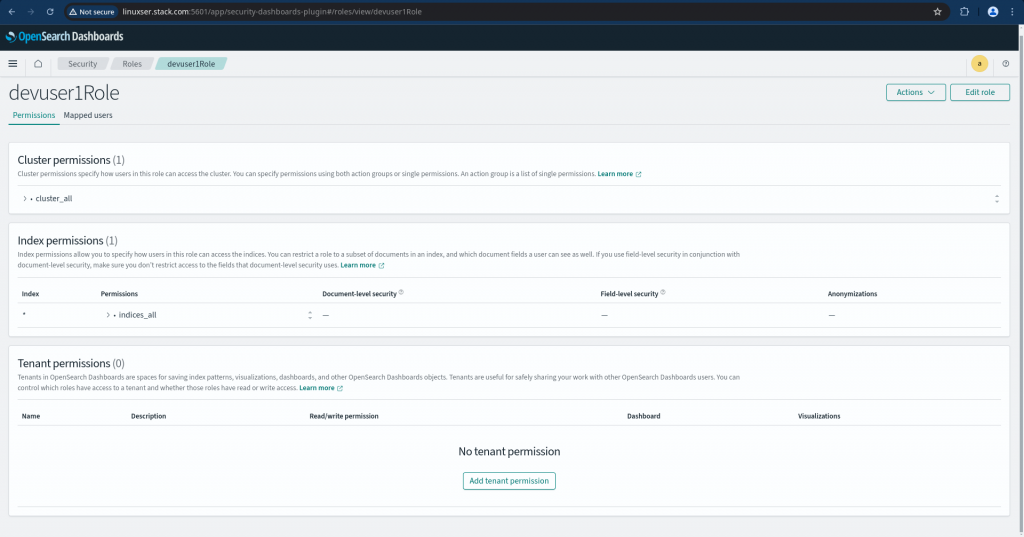
For a complete list of cluster and index level permission available to set we can refer the following documentation.
Also if you noticed carefully while selecting the permissions from the dropdown list we can select an ActionGroup which is collection of permissions. If you are unsure on which permissions need to set at granular level you can use to default Action Groups at Cluster level and Index level as per the following documentation.
Step4: Map user devuser1 to role devuser1Role
Now that we have our user and role created, the final step is to map user to role which can be done from OpenSearch dashboard by opening the role created and clicking on the Mapped users to Manage mapping. Here we can map the user to the role created as shown below.
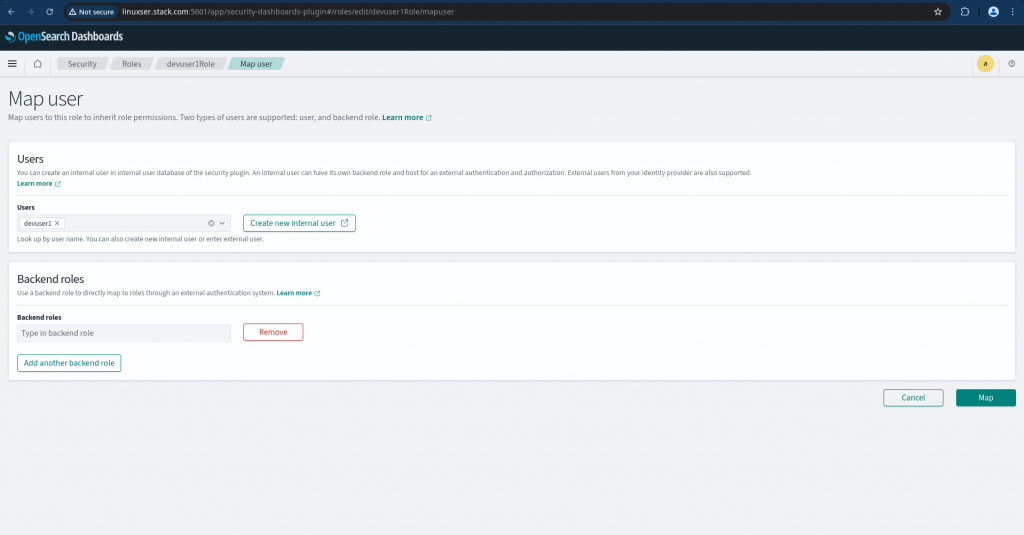
Until now, we have seen how we can create user, role and map a role to user using the OpenSearch dashboard. This procedure is good enough if you want to manage only a finite number of users. But if we want to manage users from multiple projects and team it would be wise enough to automate this procedure to improve on the productivity and reduce management time.
Step5: Manage users and roles using REST API call
Let’s first create a role file named devuser2Role.json which contains all the required cluster and index level permissions which are supposed to be assigned. Here is the sample file as shown below.
File: devuser2Role.json
{
"cluster_permissions": [
"cluster_all"
],
"index_permissions": [{
"index_patterns": [
"*"
],
"dls": "",
"fls": [],
"masked_fields": [],
"allowed_actions": [
"indices_all"
]
}]
}
Now that we have the new role with the required permission that needs to be assigned. Let me provide a bash script which we can use to create a user, role and map the user to role as shown below using the REST API endpoints.
File: userrolemapping.sh
#!/bin/bash
usage()
{
echo "======================================================================="
echo "Run the script with the following arguments as shown below"
echo "./userrolemapping.sh <adminUser> <adminPassword> <opensearchHost> <newUsername> <newRolename>"
echo "======================================================================="
}
[[ "$#" != 5 ]] && usage && exit 100
adminUser=$1
adminPassword=$2
opensearchHost=$3
newUsername=$4
newRolename=$5
# Create a new user with default password
curl -X PUT -H 'Content-Type: application/json' https://$opensearchHost:9200/_plugins/_security/api/internalusers/$4 -d '{ "password" : "Sustain@92345" }' -u $adminUser:$adminPassword --insecure
echo -e "\n"
# Create new role
curl -X PUT -H 'Content-Type: application/json' https://$opensearchHost:9200/_plugins/_security/api/roles/$5 -d @$5.json -u $adminUser:$adminPassword --insecure
echo -e "\n"
# Map new user to new role
curl -X PUT -H 'Content-Type: application/json' https://$opensearchHost:9200/_plugins/_security/api/rolesmapping/$5 -d '{ "users" : ["'$4'"] }' -u $adminUser:$adminPassword --insecure
echo -e "\n"
This script is accepting 5 parameters whose details are as provided below.
- adminUser – This is the admin user name which get created by default with first time setup of OpenSearch
- adminPassword – This is the corresponding password for the admin user
- opensearchHost – This is the Fully Qualified Domain Name of the OpenSearch cluster
- newUsername – The new user name which we want to create
- newRolename – The new role which we want to create. Make sure the role name matches with the role file name which we created earlier
Let’s now try to run the above script with all the required parameters as shown below.
$ chmod 755 userrolemapping.sh
$ ./userrolemapping.sh admin Se@rch@2025 linuxser.stack.com devuser2 devuser2Role
Output:
{"status":"CREATED","message":"'devuser2' created."}
{"status":"CREATED","message":"'devuser2Role' created."}
{"status":"CREATED","message":"'devuser2Role' created."}
As you can see the following script has created the user, role and mapped them which you can validate from the OpenSearch dashboard also.
If you try to execute the script again with the same inputs, it just updates the objects as per the provided inputs.
$ ./userrolemapping.sh admin Se@rch@2025 linuxser.stack.com devuser2 devuser2Role
{"status":"OK","message":"'devuser2' updated."}
{"status":"OK","message":"'devuser2Role' updated."}
{"status":"OK","message":"'devuser2Role' updated."}
Hope you enjoyed reading this article. Thank you..
Leave a Reply
You must be logged in to post a comment.