Oauth2.0 Client Credentials Workflow

Here in this article we will try to understand about the Oauth2.0 Client Credentials Workflow which is used in communication between two API services or servers without user interaction.
Client Credentials Workflow
The Client Credentials Flow in OAuth 2.0 is designed for machine-to-machine (M2M) communication where no user is involved. This flow is commonly used when a server application (client) needs to authenticate itself and access resources on another server (resource server).
Scenario: Payment Gateway Integration
Let’s consider a scenario in which you’re building an e-commerce platform, and your server needs to interact with a third-party payment gateway’s API (such as Stripe or PayPal) to process payments. This interaction doesn’t involve a user logging in — it’s purely server-to-server communication.
High Level Architecture
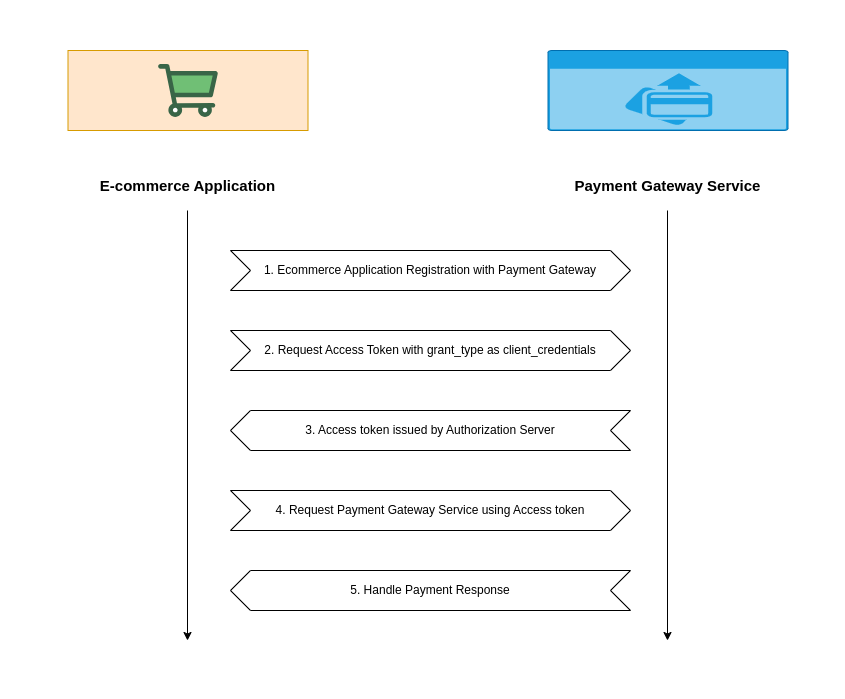
If you are interested in watching the video. Here is the YouTube video on the same step by step procedure outlined below.
Step-by-Step Example
Step1: Register the Client Application
- The e-commerce platform (your server) registers with the payment gateway (authorization server).
- During registration, the payment gateway provides:
- Client ID: A public identifier for your e-commerce platform.
- Client Secret: A private key that your server uses to authenticate itself.
Step2: Request an Access Token
When your server needs to call the payment gateway’s API, it sends a POST request to the payment gateway’s token endpoint with the following data:
- Grant Type:
client_credentials - Client ID: The ID issued during registration.
- Client Secret: The secret issued during registration.
- Scope: The permissions your server is requesting (e.g.,
payments:write).
Example Request:
POST https://payment-gateway.com/oauth/token
Content-Type: application/x-www-form-urlencoded
grant_type=client_credentials&
client_id=YOUR_CLIENT_ID&
client_secret=YOUR_CLIENT_SECRET&
scope=payments:write
Step3: Authorization Server Issues an Access Token
- The payment gateway validates the client ID, client secret, and requested scope.
- If valid, it responds with an access token.
Example Response:
{
"access_token": "ACCESS_TOKEN",
"token_type": "Bearer",
"expires_in": 3600,
"scope": "payments:write"
}
Step 4: Use the Access Token to Access Resources
- Your server uses the access token to make authorized API requests to the payment gateway.
Example API Request:
POST https://payment-gateway.com/api/v1/payments
Authorization: Bearer ACCESS_TOKEN
Content-Type: application/json
{
"amount": 100.00,
"currency": "USD",
"payment_method": "credit_card",
"description": "Order #12345"
}
- The payment gateway’s resource server validates the access token and processes the request.
Step 5: Handle the Response
- The payment gateway responds with the result of the API request (e.g., confirmation of payment processing).
Example API Response:
{
"status": "success",
"transaction_id": "txn_987654321",
"amount": 100.00,
"currency": "USD"
}
Key Features of Client Credentials Flow
- No User Involvement:
- This flow is used exclusively for server-to-server communication, so no user authentication is involved.
- Access Token Usage:
- The access token is used to authorize API requests.
- Secure Storage of Secrets:
- The client secret must be securely stored by the client (your server) and never exposed in public repositories or client-side code.
- Short-Lived Tokens:
- The access token typically has a short lifespan, reducing the risk of misuse.
Common Use Cases
- Payment Gateways: Server-to-server API calls to process payments.
- Data Sync: Syncing data between two backend systems (e.g., CRM to ERP system).
- Job Monitoring: A server polling or pushing updates to a monitoring system.
- Cloud Service Automation: Accessing cloud resources and APIs (e.g., AWS, Google Cloud).
This flow is widely used in backend integrations where secure and automated communication between servers is required.
Hope you enjoyed reading this article. Thank you..
Leave a Reply
You must be logged in to post a comment.